Maritime Cyber Security : variable summary card
Maritime Cyber security
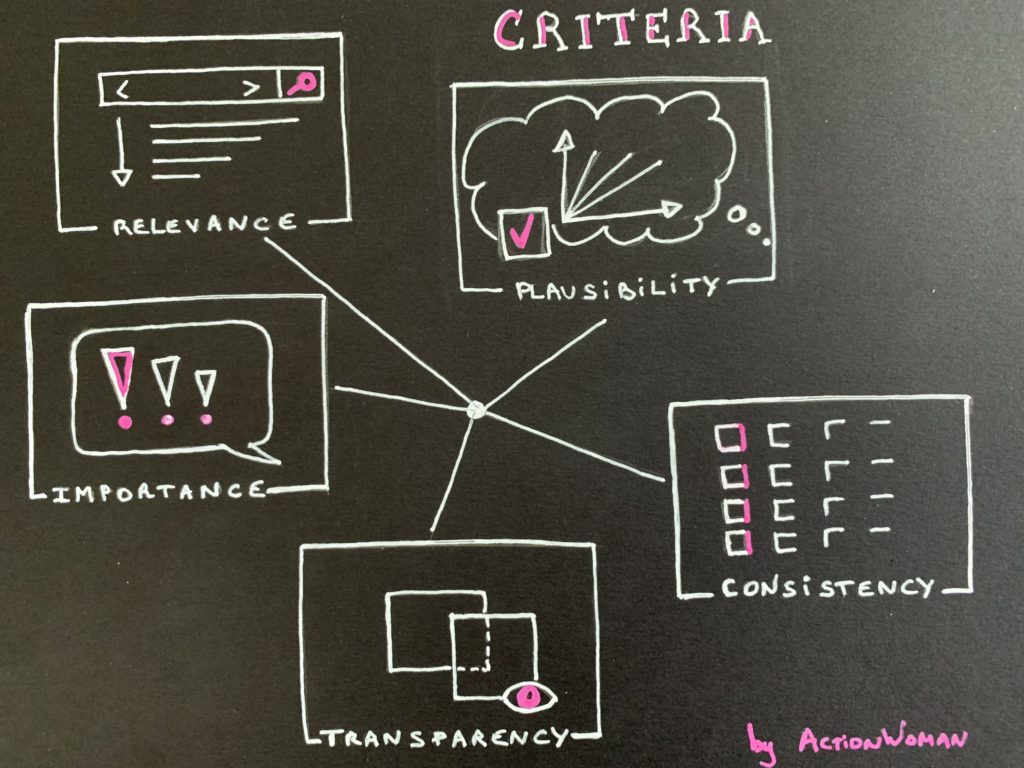
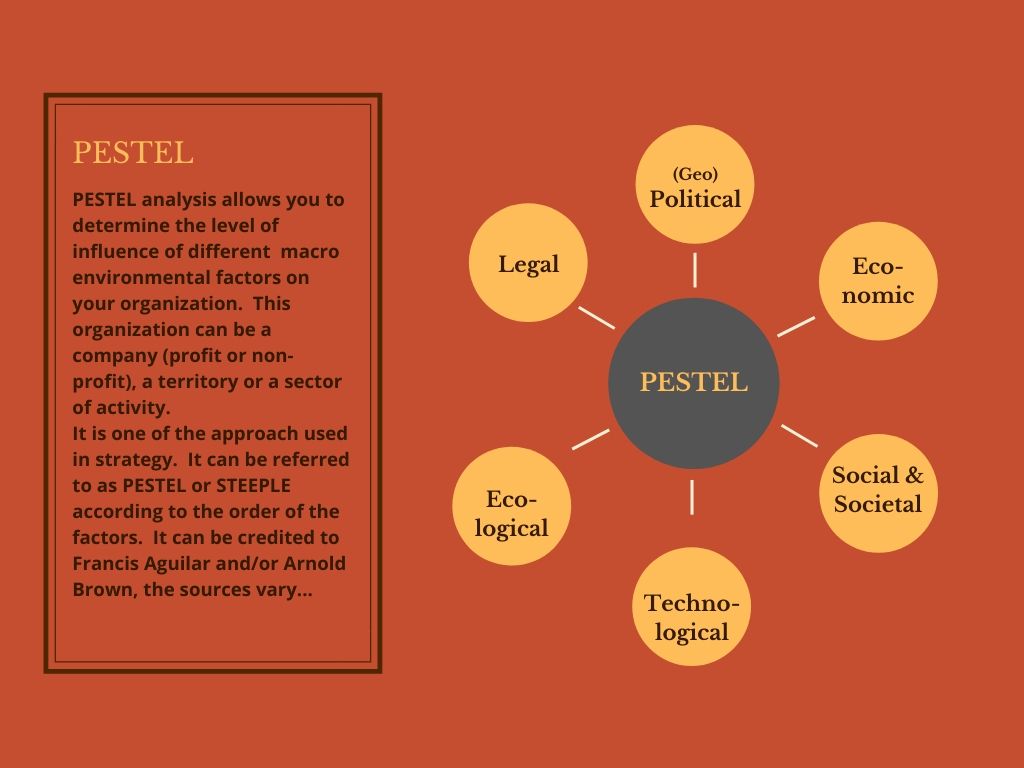
This summary card presents the Maritime Cyber Security variable: how is it defined, what are the relevant indicators to assess it, what are the remarkable historical facts, who are the interested parties, where are the links for a foresight study. Hypotheses still need to be developed to be complete…
This series of publications are extracted from my final paper written within the frame of university certificate on foresight (UCL – Sept 2018)
Maritime Cyber security : variable definition
Originally, maritime security includes surveillance, protection and security activities aimed at combating piracy on board ships.
Over time, threats have become more diverse and digitalized. While digitization has increased the profitability of the maritime sector, it also implies particular security.
ENISA therefore recommends that maritime procedures be amended to include cyber-risks.
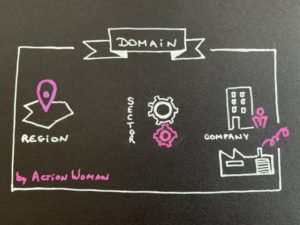
At the country level, everyone is concerned because a problem in the smallest country can cause problems for the biggest.
At the activity level, the following are concerned:
- Ship management
- Cargo management
- Intra-port management
Relevant Indicators
- Protection of digital equipment (e.g. SCADA – Supervisory Control And Data Acquisition)
- Level of security awareness among the crew (training + test for example)
- Evolution of threats: types, levels, impact and likelihood (via regular audits)
- Evolution of weak points (access)
- Number of security incidents + breakdown into categories (# cyber-attacks, …)
- Number of shipwrecks due to cyber sabotage
- …
Experts estimate the reported cyber incidents at 10% of the real number; on the one hand to avoid increasing insurance premiums, on the other hand to protect one’s reputation.
Retrospective
Today, many installations are vulnerable because at the time of their implementation, the cyber risks were unknown.
In 2004, ENISA, the European Network and Information Security Agency, was created by a European Union regulation and is based in Heraklion.
In 2008, a first white paper on defence and security is published in France.
In 2011, ENISA publishes a report concluding that « cyber-security awareness » is very low in the maritime sector.
At the same time, the port of Antwerp suffered a cyber-attack orchestrated by a drug cartel in order to hide their products in containers and retrieve them « safe and sound » and that the « Islamic Republic of Iran Shipping Lines » had its cargo data erased by an unknown actor. These are just two of many examples.
It will not be until 2014 that maritime transport will sound the alarm.
In order to design a robust system from the outset, harmonization and standardization would be desirable, especially as information and communication technologies in the maritime environment are very complex.
This harmonization should involve the 3 levels of governance: international, European and national.
It is necessary to go beyond the purely physical aspects of security.
A risk-based approach is desired.
Involved stakeholders
- International Maritime Organization
- EU Commission
- Member States
- Police
- Shipowners
- Carriers
- Customs
- Logisticians
- …
Foresight
Vessels
Ships have many digital technologies.
It is mandatory for them to be equipped with electronic navigation systems (SOLAS convention). Authentication is crucial for communicating information necessary for safety at sea, but it is non-existent. An integrated bridge (sea-shore) brings together the different navigation systems. The infrastructures on land are therefore also concerned…
Threats can be of various kinds; they can be intrusion for commercial espionage => access to the cargo manifest. Hackers/pirates then make an informed choice of targets for physical attacks.
It can also be sabotage with taking control of the digital gateway.
Ports
Ports are a prime target along with airports and nuclear power plants. They fulfil 4 functions:
- Nautical activity
- Goods logistics
- Industrial activity
- Human dimension
The exchange of information takes place at these 4 levels and the speed of vessel and freight management is a factor of competitiveness. Consequently, exchanges between the various stakeholders must be fluid. The trend is towards a « smart port » concept.
New vulnerabilities are emerging with new « disruptive » factors:
- Infrastructure security
- Port Security
- Operation of the port affecting its reputation
The port becomes the weakest link in the supply chain …
Satellite risks
The accident (shipwreck) rate has been divided by 8 in 100 years. Applications are constantly developing but they are certainly targets for cyber criminals, whether civilian or military.
Sources, Useful links & Resources
Enisa.europa.eu
Vitel P. (20/03/2018). Conférence Cybersécurité et milieu maritime : état des lieux et prospectives. Paris. Ecole de Guerre économique.
Pauquet W. et al. (09/03/2017). Note Stratégique : cybersécurité dans le milieu maritime : défis et pistes de solutions. www.observatoire-fic.com
Loi du 02/10/2017 sur la sécurité privée et particulière
AR 11/06/2013 : carte, journal de bord, rapport de mission
AR 02/09/2013 : autorisation entreprise
AR 01/12/2013 : formation
AR 04/09/2013 : lutte piraterie